How to Test API Endpoints Using an HTTP Client on macOS
Learn how to use Devknife's built-in HTTP client to send requests, inspect responses, and test your APIs, all within a fast and private native macOS app.
Read MoreNmap is one of the most powerful and widely used tools for network exploration and security auditing. From scanning open ports to identifying services and operating systems, it gives you a detailed view of what’s happening on a network.

Classic Nmap ASCII logo shown in the terminal.
The catch is that Nmap is a command‑line tool. While that makes it extremely flexible, it can also feel intimidating if you’re not comfortable with terminal commands. Even for experienced users, running scans from memory or looking up syntax every time can slow you down.
That’s where a graphical interface helps. A simple, native macOS GUI makes Nmap more approachable, faster to use for everyday checks, and easier to learn for people just starting out.
For many years, the most familiar Nmap GUI has been Zenmap. It offers a lot of features and is well known in the security world. Zenmap is still available but the installation process isn’t smooth on macOS, and visually it doesn’t look like a Mac app at all since it’s built with the GTK toolkit, making it look more like a Linux application.
The CLI version of Nmap is powerful and flexible, but it comes with a steep learning curve. Many users struggle with remembering the right flags and options, which can make everyday tasks slower and less approachable.
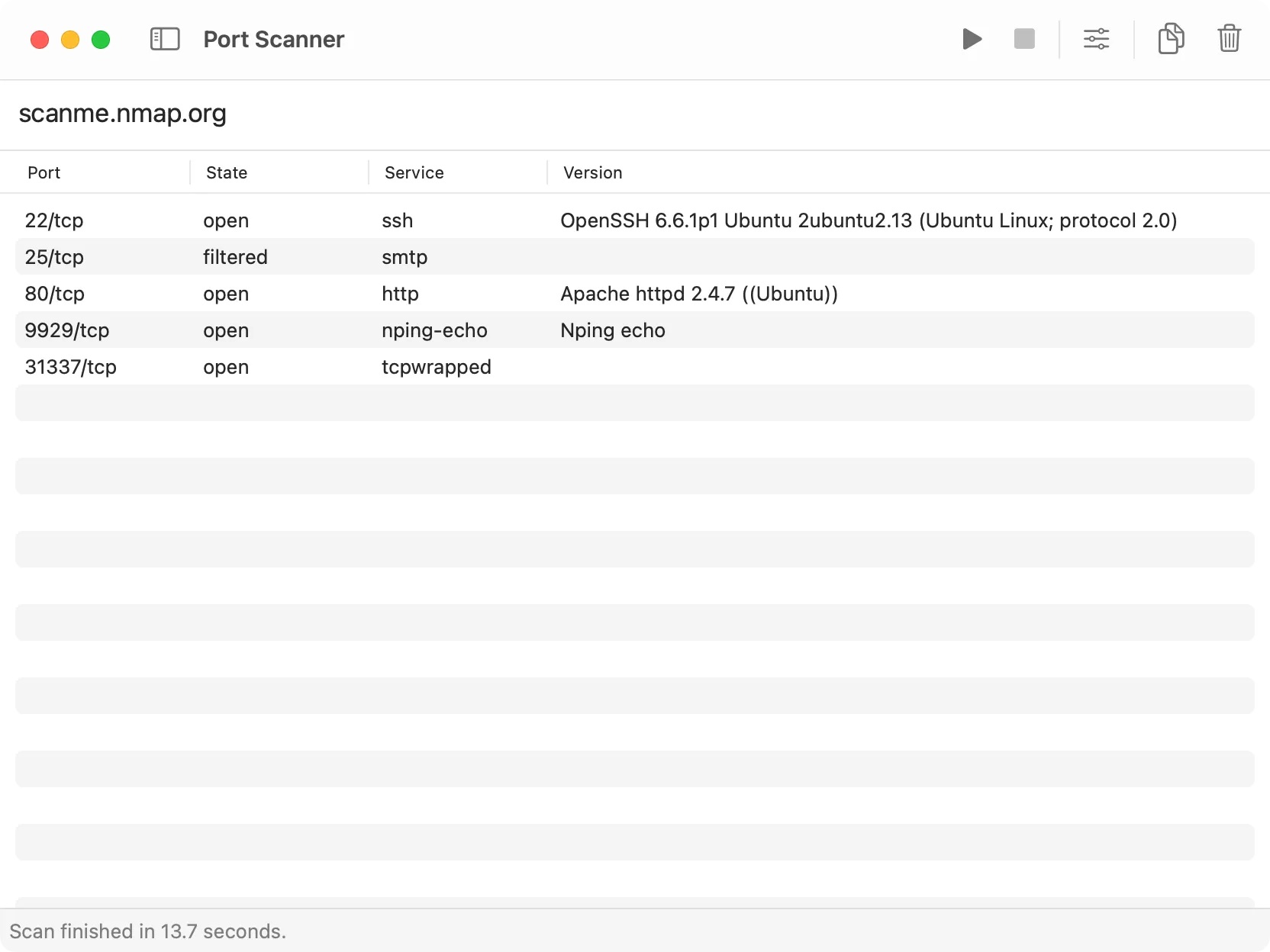
Port scanning with Nmap, but through DevKnife’s clean macOS interface.
This is where DevKnife comes in. It’s an all-in-one developer toolkit for macOS that includes a Port Scanner built on top of Nmap. You still get the full power of Nmap under the hood, but wrapped in a clean, native interface that feels at home on macOS. Instead of memorizing command-line options, you can run quick scans or dive into advanced ones with just a few clicks.
DevKnife runs Nmap under the hood, but hides the messy parts behind a simple, native UI. The basic flow is always the same: choose a scan mode, type a target (IP or hostname), tweak a couple of options if you need to, and hit Start. Results appear in a readable panel as the scan runs — open ports, service names/versions, and (when available) OS hints and extra notes.
Standard scan — fast, no elevated privileges required. Use this for quick connectivity checks (is port 80 open? is my service reachable?). It uses safe, non-privileged scan types so it works out of the box on macOS.
Stealth scans — includes SYN stealth scans, OS detection, and some service probes. These require root privileges to run properly. Use them when you need deeper information (service fingerprinting, OS guesses, stealthy probes).
In the UI you can pick the scan type and tweak a few common options without having to learn Nmap flags:
If Nmap is not installed yet, you can install it quickly with Homebrew:
brew install nmapor download it from the official site. DevKnife will detect the nmap binary location automatically.
DevKnife gives you the full power of Nmap without the rough edges. Compared to the command line, you don’t need to remember long flag combinations or keep a cheat sheet open. Everything you actually need is right there in the UI, ready in a couple of clicks.
Against Zenmap, DevKnife feels at home on macOS. It’s lightweight, clean, and easy to install — no GTK windows, no dated look. It works fully offline (the only traffic is to the target you scan), and it’s actively maintained as part of the wider DevKnife toolkit.
Nmap has always been a go-to tool for network scanning, but its command-line nature makes it less approachable for everyday use. DevKnife brings that same power into a clean, native macOS interface — giving you the results you need without the overhead.
If you’ve ever wanted the strength of Nmap with the simplicity of a GUI, give DevKnife a try and see how much smoother your workflow can be.
Learn how to use Devknife's built-in HTTP client to send requests, inspect responses, and test your APIs, all within a fast and private native macOS app.
Read MoreLearn how to create MD5 and SHA hashes on macOS using built-in commands or DevKnife’s Hasher tool.
Read MoreNeed to convert Unix timestamps on your Mac? Discover the fastest, most secure, native method using DevKnife's new Time Inspector tool. Skip the browser tabs!
Read More
Fast, private, and built for macOS.